![]()
Don’t let cybercriminals exploit weaknesses in your network.
TARA is committed to helping you safeguard your organization’s sensitive data.
TARA identifies, quantifies, and communicates evolving cyber risk in the enterprise. By combining network vulnerability data with intelligence from global threat research, TARA pinpoints and prioritizes the risk you need to mitigate. Our platform utilizes predictive AI to deliver true risk-based vulnerability management as well as ongoing third-party risk validation.
Predict where risk is growing and will evolve in your environment.
Save your company time and money.
Eliminate the most cyber risk.
TARA is a Cloud Hosted Platform that identifies and quantifies leading causes of data breaches and ransomware.
Our risk-based vulnerability management platform shifts organizations to a proactive strategy that reduces mitigation efforts and dramatically improves risk coverage.
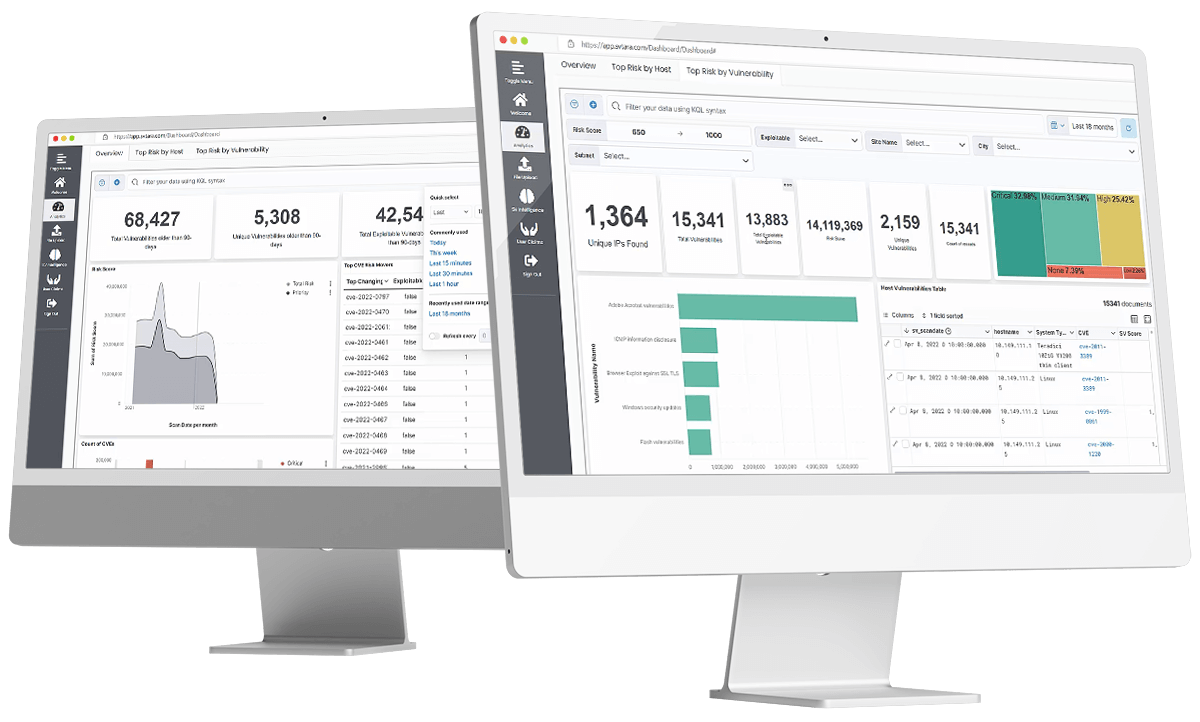
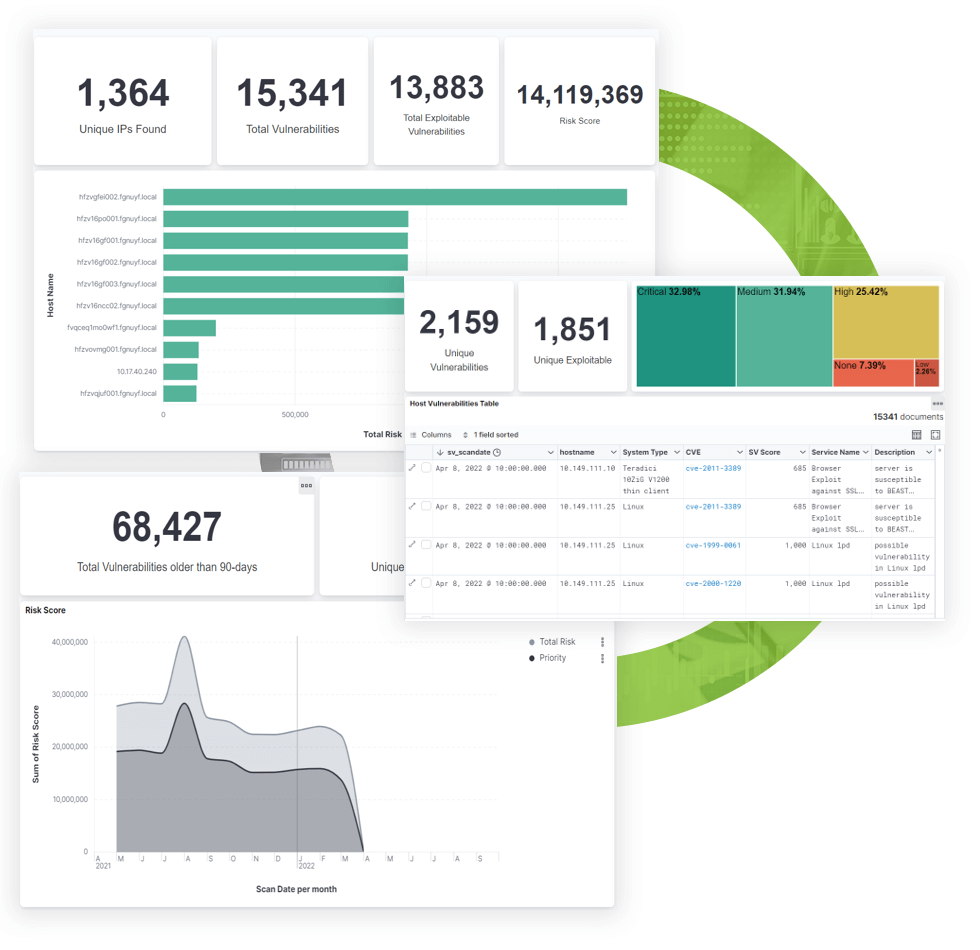
TARA ingests data directly from industry leading scan engines and delivers in-depth risk scoring.
A graphically rich dashboard transforms the data to provide performance trending, prioritized mitigation recommendations, and in-depth CVE intelligence.
Organizations that use the risk-based vulnerability management method will suffer 80% fewer breaches.
*Source: Gartner, “A Guide to Choosing a Vulnerability Assessment Solution,” April 2019