Risk-based vulnerability management (RBVM) is a cybersecurity approach that allows organizations to prioritize remediation based on the actual risk of each vulnerability.
Unlike legacy vulnerability management, risk-based vulnerability management does not just reveal vulnerabilities; it quantifies them with a threat context and potential business impact awareness.
RBVM uses threat intelligence to identify the vulnerabilities attackers are discussing, experimenting with, or using, and generates risk scores based on the likelihood of exploitation. By contrast, the legacy Common Vulnerability Scoring System (CVSS) rates vulnerabilities based on the damage they would do if exploited. Time has demonstrated that many vulnerabilities with high CVSS scores pose little to no risk of ever being exploited. Given this low probability, directing resources toward risk-verified vulnerabilities reduces mitigation efforts and increases risk coverage.
Most organizations struggle to prioritize vulnerability scan results and use a “legacy” approach that remediates Critical and High (CVSS Ranking) vulnerabilities.
TARA is suited to meet the needs of organizations that need a turn-key managed vulnerability program as well as those that want a risk-based view to improve prioritization of existing scan data. For firms that want to invest resources to maximize risk coverage, TARA’s data-driven approach delivers results:
A full-service approach that includes installation, configuration, and ongoing management of scanning software as well as a client-specific, risk-based vulnerability dashboard.
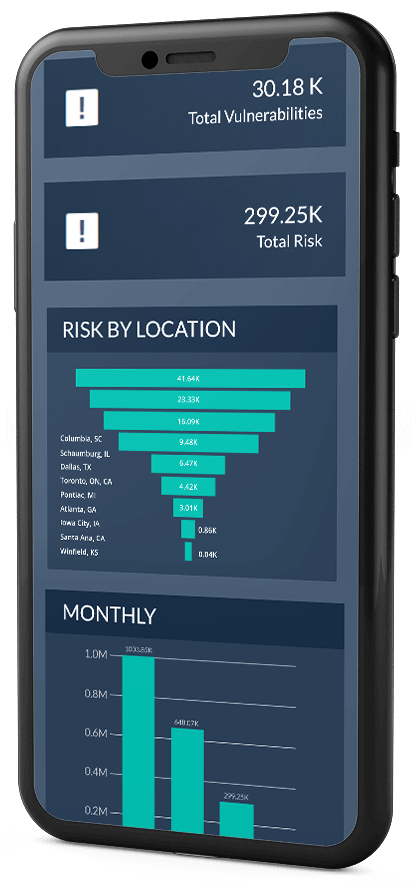
Findings are segregated by mitigation group or location to provide clear priorities for the patching teams.
Software as a service that ingests vulnerability data from scanner technologies, enriches it with threat intelligence, and delivers risk-based scoring in a client specific dashboard. Findings are segregated by mitigation group or location to provide clear priorities for the patching teams.
Our Mitigation Support service provides you with monthly meetings to review risk scoring, discuss questions about findings, evaluate progress, and refine mitigation priorities.
Understanding which vulnerabilities are the riskiest is the secret to effectively utilizing mitigation resources. TARA provides risk insights that can reduce mitigation workload by 90% or more.
Click on the steps below to understand more.
TARA utilizes global threat research to understand how attack techniques are evolving.
Intelligence is fed into a powerful AI engine that predicts the probability and likelihood of a vulnerability impacting your environment.
A unique risk score is assigned to each vulnerability.
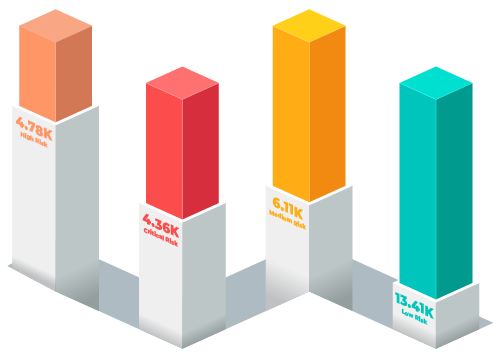
All vulnerabilities are summed to create an enterprise risk score.

Results are displayed in graphically rich dashboards tailored to your organizational structure.